TRACK YOUR AWS SPEND WITH TAG ENFORCEMENT: SERVICE CONTROL POLICIES AND CLOUDFORMATION FOR COST REPORTING

Establishing a proper tagging taxonomy is an important early component of any AWS project. A good tagging strategy allows for efficient data organization and enables end users to easily identify groups of resources. When used properly, it also helps AWS users understand where their dollars are being spent across departments and projects. However, reliable spend data requires consistent tagging by each user touching the account. So how do you enforce proper tagging across an entire organization?
Tagging Costs with AWS
Let’s start with AWS’s cost tagging capabilities in general. AWS offers the Cost Allocation Tag which can be leveraged in the AWS Cost Explorer to identify all costs associated with a particular tag. For example, consider an AWS account that is shared between multiple departments and whose costs need to be charged back to the department that originated the spend. The cost allocation tag of “costcenter” can be used along with values of “departmentA,” “departmentB,” etc.
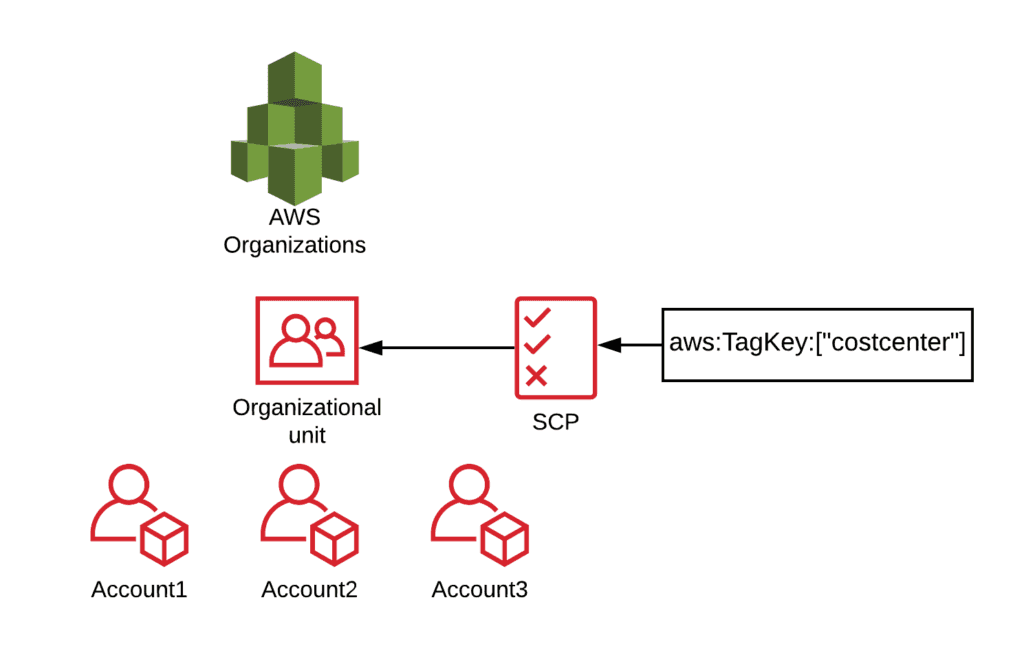
An architecture of how to implement the SCP at the AWS Organization level. In this example, it is applied to Accounts 1, 2, and 3.
Tag Enforcement with Service Control Policies
In order for tags to work, they have to be applied regularly and consistently. AWS Organizations’ Service Control Policies (SCP) can be used to enforce cost allocation tagging. AWS Organizations allows administrators to organize their child AWS accounts into groups called Organizational Units (OUs). Administrators can then apply appropriate SCPs that allow and deny permissions within each OU. The Conditions block within the SCP at this level are fairly granular, creating specific logic for what to deny based on ‘xyz’ Conditions. The administrator can then add a global parameter of “aws:TagKeys” (available under the Conditions block) to check API calls for tags specified. SCPs can be created to deny events such as “RunInstances” for EC2 when the “aws:TagKeys” Condition does not find a specified key—such as the cost allocation tag key.
Unfortunately, this process does not work with all AWS resources because not all resources (like S3 buckets for example) allow for the specification of tag keys during creation.
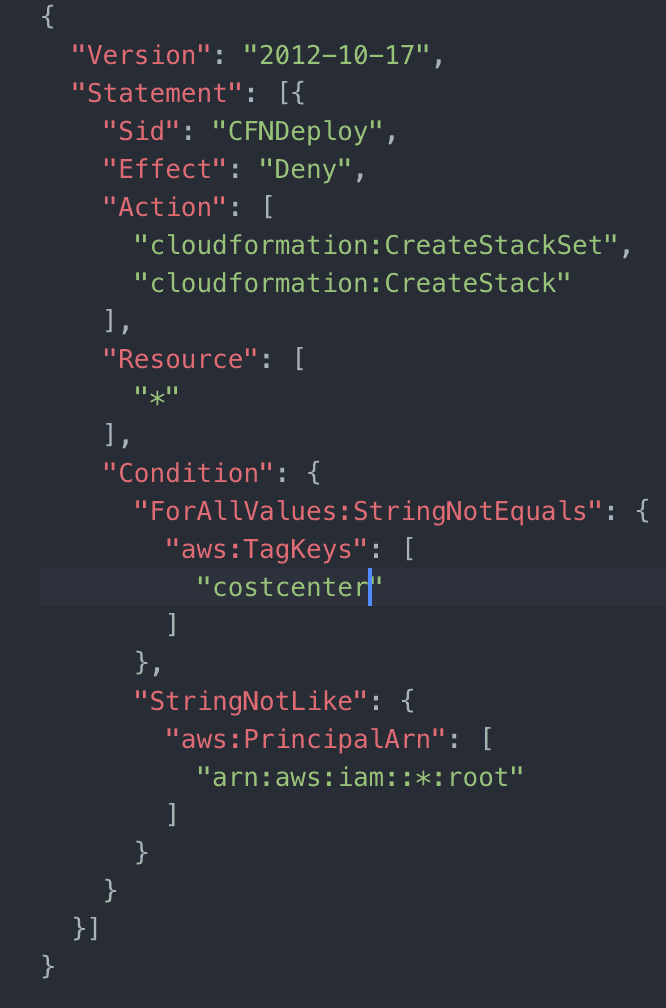
Tag Enforcement with CloudFormation
The solution for resources that do not allow for specification of tags during key creation is using AWS CloudFormation for creating resources. When deploying CloudFormation stacks, users can specify tags which can be retroactively added to the resources the stacks are deploying.
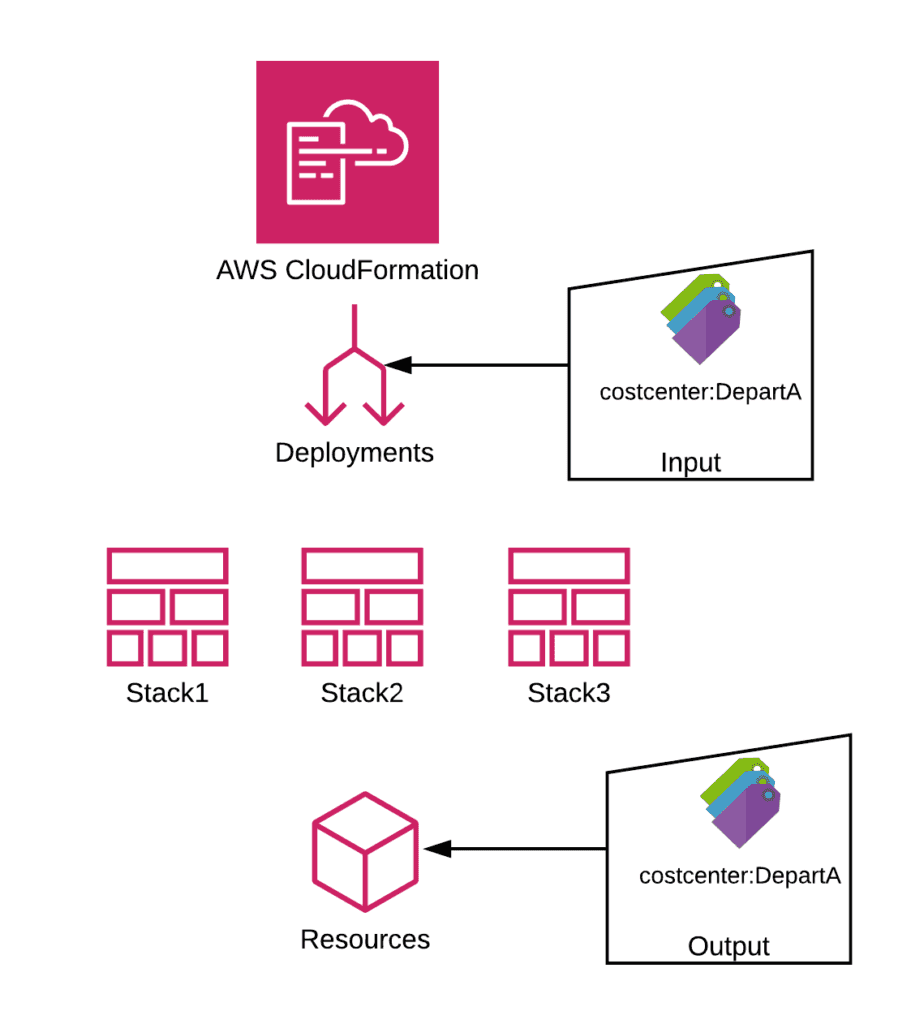
By applying an SCP to deny CloudFormation stacks from being created when a particular tag is not specified, administrators can have deeper control over tag enforcement and deliver more robust, accurate cost reporting.
