BRINGING RISK INTO VIEW: A GUIDE TO MORE EFFECTIVE VENDOR RISK MANAGEMENT

Managing vendor risk has become a challenging standard practice for most organizations today. With the adoption of cloud technologies and globalization of technology service providers, more companies are working to evaluate the security programs of vendors and service providers as well as gain visibility of vendor risk overall. Whether you are tasked with evaluating a vendor’s security program or responsible for maintaining visibility of enterprise vendor risk, both functions present challenges and barriers. Among these challenges, one of the most difficult for organizations to navigate is completing security questionnaires for partners or clients dependent upon their services, as no single industry or company has adopted a widely used standard for the process. This results in teams receiving lengthy questionnaires that all differ in volume and complexity.
Another key challenge arrives for companies needing to establish a process for maintaining holistic, enterprise-level visibility of vendor risk. The present reality is that most companies find themselves burdened by both of these processes. Below, we’ll explore actionable steps to reduce the difficulty of managing vendor security and risk questionnaires, and steps to enhance the security of your organization through establishing a vendor due diligence review process.
Simplifying Security Questionnaire Response
Multiple solutions exist to mitigate the challenge of performing vendor security assessments, but very few address the burden of completing security questionnaires. However, you can greatly reduce this burden by doing the following:Create a Repeatable Process
- Gather all information about the controls in your environment and provide the same questionnaire to all requestors
- Eliminate questions not applicable to your business, operations, and environment
- Keep answers short and simple
- Create an encrypted, password protected, and centralized repository that includes public-facing/redacted policy/program documents, attestations, security compliance overview presentations, and a single version of your questionnaire
- Recognize that offering too much information, screen shots, or tool-specific responses can exacerbate the problem
- Ensure that all questions offer consistent responses whenever possible
Recognize That Certification Attestation Can Validate Strength of Control Environment
- Understand how certification (SOC2, ISO, NIST) can help – many topics covered in questionnaires are also covered in the control attestation process
Recognize Liability Associated with Security Questionnaires
- Acknowledge that security questionnaires can be traced to liability risk, which may be inevitable for some organizations
- Upon completing the questionnaire, any future incident may prove a question was answered incorrectly, and organizations can be held liable for negligence or misrepresentation of the “secure” environment
- When evaluating the security of another organization, any future incident may prove a questionnaire and risk assessment process to be inadequate, and companies can be held liable for failing to perform an appropriate level of due diligence in vendor selection or monitoring
Proactively Avoid Missed Business Opportunities
- If gaps are identified in your responses, include a remediation plan with a target date for completion (to prevent voiding potential business opportunities)
- At minimum, this will show that your assessment processes are functioning and that there is already a plan in place to address self-identified control gaps
Achieving Holistic Vendor Risk Visibility
If you are struggling to understand your organization’s vendor risk holistically, there are many solutions that can help. As with any great automation capability, process is paramount. Consider the following recommendations to raise your organization’s awareness of vendor risk:Establish a Policy or Standard
Begin with a policy or standard for evaluating vendors based upon your organization’s expectations (or regulatory requirements). The policy or standard should be framed by risk exposure and include:- What conditions or criteria determine the level of risk associated with a service provider
- Which reviews are performed relative to the level of risk associated with each service provider
- How frequently risk will be assessed (e.g., if a vendor is high-risk, consider performing annual reviews; if a vendor is low-risk, consider performing bi-annual reviews)
Categorize Vendors by Risk
What conditions or characteristics need to be understood to categorize vendors by level of risk? As usual, it depends! If your organization has an appropriately structured Enterprise Risk Program, it is likely that these conditions and characteristics are already outlined in what is typically referred to as a risk tolerance or risk threshold statement within your risk management framework or risk assessment methodology. On the other hand, if your organization does not have a well-defined Enterprise Risk Program, you may not have achieved a level of growth that warrants one (yet). The good news is that you can inspire risk reduction specific to IT security by establishing a risk assessment methodology that centers around information security risk (availability, confidentiality, integrity). For an information security-centric approach, consider the following:Availability Risk
- Is the service provider providing something that is critical to the operation of my business?
- If this service is interrupted, would the impact to my operations be extensive or minimal?
Confidentiality/Integrity Risk
- Is the service provider storing, processing, or transmitting sensitive data?
- Has your organization defined what sensitive data is?
- PCI, PII, patents, trade secrets, PHI, etc.
- Has your organization defined what sensitive data is?
Establish a Consistent, Risk-Based Approach
Depending on your answers to the two questions posed above, you’ll need to determine how extensive of a review is warranted. The table below can be used as a guide when establishing a risk-based approach to perform vendor risk assessments.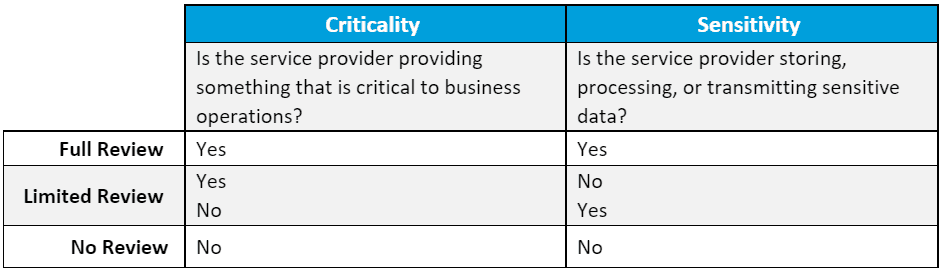
It is worth noting that ‘Limited,’ in this context, does not mean ‘less’ review. Rather, it means asking tailored questions directly associated to criticality and/or sensitivity – whichever applies per engagement. The point here is that if a review process were defined and issued to all vendors regardless of criticality or sensitivity (using the aforementioned ‘broad-brush’ approach), you would spend time requesting, collecting, and reviewing information that offers no real value to the organization.
For example, if a service provider is not providing a critical service, do you need to see a record of successful recovery testing? Conversely, if a service provider is not storing, processing, or transmitting any sensitive data on behalf of the company, do you need to validate that encryption is used?
Additional Considerations for the Vendor Risk Review Process
The following considerations may be helpful in defining a review process; all provide opportunities to reduce the burden of effort associated with performing vendor risk assessments:- Include business purpose information, such as source departments, relationship sponsors, relevant technology or applications, and dependent business processes. Identifying these factors early on will make it easier to validate recovery capabilities or necessary data protections.
- Include questions that assess how critical a service is to validate that a vendor’s recovery capabilities are sufficient. If it is highly critical to operations, this may serve as justification to perform the review more frequently, or to gather information from process owners to determine if contingency plans exist internally. For example, if the service is non-critical, are business continuity and disaster recovery documents or associated questions necessary when the contract itself stipulates SLA language specific to recovery capabilities?
- Identify what data is being stored, processed, or transmitted. If highly sensitive data (such as PCI or HIPAA) is involved, you may want to perform the review more frequently or consider specific data protection controls that must be validated before a service engagement proceeds.
