INTEGRATING HCP VAULT WITH TERRAFORM CLOUD BUSINESS & GOOGLE CLOUD PLATFORM

Part of what makes the partnership between AHEAD and HashiCorp so special is our constant drive to collaborate, innovate, design, and implement solutions. Through our partnership with ServiceNow, combined with HashiCorp’s products—particularly Terraform Cloud Business (TCB) and HashiCorp Cloud Platform Vault (HCP Vault)—we have a unique opportunity to drive significant value for our customers. Recently, HashiCorp and AHEAD engineers collaborated on a ServiceNow workflow that calls a TCB workspace, gathers dynamic secrets from HCP Vault, and provisions a GCP workload with a sample software stack—all from one request. To achieve this, a lot of work had to happen behind the scenes. In this article, we’ll examine the use case, design, deployment, and what this means for our customers.
HCP Vault
HashiCorp Cloud Platform Vault (HCP Vault) is HashiCorp’s managed Vault offering, giving customers all of the power and security of Vault, without the complexity and overhead of managing it themselves. This option allows customers to focus on driving value through Vault Enterprise features without worrying about the environment, maintenance, and downtime. Because both ServiceNow and TCB also run in the cloud, HCP Vault was an obvious choice for the integration use case. See https://cloud.hashicorp.com/products/vault for more information.
Terraform Cloud Business (TCB)
During the design phase, AHEAD and HashiCorp chose to use TCB to host the Terraform modules that are responsible for the creation of the Vault Environment and the workload. Given TCB’s integration with ServiceNow, this was a sensible choice for our demo environment. We partitioned our demo environment into several workspaces in addition to spinning up modules that could automatically create HCP Vault namespaces and configure secrets engines (in our case, the GCP engine) with a terraform apply command.
We used the HCP Provider for Terraform built by HashiCorp and an HCP module to deploy the HCP Vault cluster. We then used the HashiCorp Vault Provider for the admin configuration, namespace creation, policy generation, and secrets engine configuration. This allowed us to automatically query HCP Vault for a dynamic secret for GCP. Showing how dynamic secrets can be created, used, and destroyed within a given time frame for infrastructure provisioning was of great interest to us and our clients, and a use case we feel will have a wide range of applications across cloud infrastructure.
Finally, TCB allows us to show off the differences between Auto-Apply and a manual approval process, and can also demonstrate HashiCorp Sentinel’s policy as code feature, such as checking for disallowed GCP machine types.
ServiceNow Integration
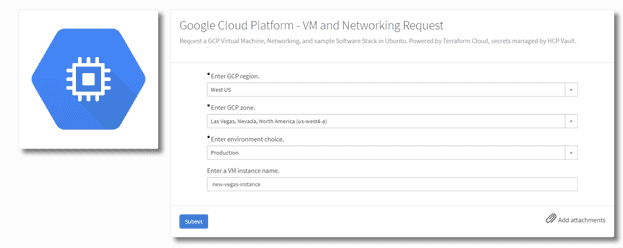
Our ServiceNow workflow involved using the Terraform Cloud integration for ServiceNow, creating a custom catalog item with variables, and configuring the ServiceNow flow to appropriately pass the information over to the TCB REST API with the correct endpoint. To configure the integration properly, we needed to set up the flow in the Flow Designer to call the correct TCB API endpoint. Authentication for TCB is handled through configuration in ServiceNow for the Terraform Cloud integration itself – we simply needed to generate a few OAuth tokens and supply them in the configuration page.
Because TCB uses HCP Vault to generate dynamic credentials for GCP authentication, our workflow in ServiceNow can simply focus on the user interface and gathering required information from the user. Supplying dropdowns in the catalog item provides users with freedom when choosing regions, zones, and environment types, while allowing Infrastructure as Code developers and administrators to put guardrails around what kinds of infrastructure can be provisioned by a user.
For instance, the environment choices (Development, Test, and Production) align to a machine_types map variable in the Terraform module, which looks like this:
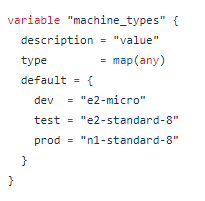
Users in ServiceNow don’t need to know exactly how the environments map to the GCP machine types, and administrators are free to add or update machine type options in TCB with minimal changes to the ServiceNow catalog item.
Google Cloud Platform Integration
The last piece to build was the Terraform module for the Google Cloud Platform integration. During the Terraform run, the Terraform agent logs into HCP Vault to retrieve dynamic credentials for use in GCP. Once these credentials are retrieved, the business logic in the Terraform module is used to provision a VPC Network, Subnet, Firewall, VM Instance, SSH keys, and finally, execute a remote script on the provisioned machine.
Once the apply has completed successfully, Terraform Cloud returns an IP address and information for accessing the machine within GCP. In our demo environment, we used the Terraform remote-exec provisioner to install the Apache HTTP Server, kicked off a shell script to create a simple HTML page, and spun up the server to serve the page when the IP address was queried. In an enterprise scenario, configuration management might be handled by Chef or Puppet to pull down dependencies for business applications.
Outcome
The overall environment looks like the diagram below:
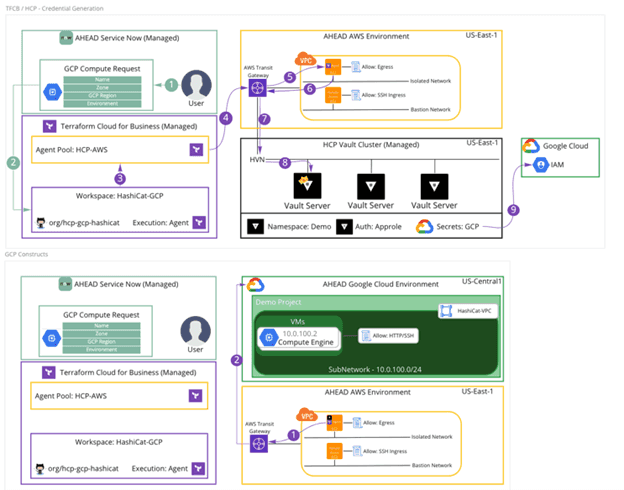
This environment helps to showcase the power of TCB, HCP Vault, and the ease in which users can self-serve infrastructure, not to mention the efficiency of Infrastructure as Code using Terraform. Going forward, this environment could be extended to use other cloud providers or infrastructure on-premises simply by configuring new secrets engines in HCP Vault and reusing Terraform modules for other environments. The goal of this setup is to build a framework for stitching services together to provide a seamless user experience for provisioning and modifying infrastructure as needed.
Conclusion
We’ve now covered an overview of the scenario, how it was built in HCP Vault, Terraform Cloud Business, ServiceNow, and Google Cloud Platform. As you can imagine, this concept can be extended to multiple scenarios and enterprise workloads depending on business needs and governance requirements. This design and configuration of HCP Vault, TCB, ServiceNow, and GCP wouldn’t have been possible without the strong partnership from HashiCorp—particularly the Partner Solution Engineering team working with AHEAD. Special thanks to them for their assistance.
AHEAD can help with the enterprise cloud journey no matter where our customers are, from getting started in the cloud to building an Automation Hub like the concept we discussed above. For more information on AHEAD’s cloud practice, visit our Cloud Platforms solutions or learn more about Automation Hub.
